Google's Project Zero Discovers 50 Security Flaws in Windows Registry

Google's Project Zero team, known for its rigorous security research, has recently concluded an extensive 20-month audit of the Windows Registry, revealing a staggering 50 security vulnerabilities.
The team's findings, detailed in a series of blog posts titled "The Windows Registry Adventure," highlight the complexity of the registry and its potential as a target for local privilege escalation attacks.
The research, led by Mateusz Jurczyk, began unexpectedly while developing a coverage-based Windows kernel fuzzer. Jurczyk's initial exploration of the registry binary format led to the discovery of two bugs, which piqued his interest in the 30-year-old, kernel-based system. This prompted him to conduct a thorough audit of the registry code.
"Windows NT 3.1 was the first system whose parts of code are still used today in Windows 11. Based on this observation, we can now confidently claim that the registry code base is over 30 years old."-Jurczyk wrote
Throughout the research, Jurczyk filed 39 bug reports to Microsoft, which were addressed as 44 CVEs. Some reports contained multiple issues, while others were grouped together and fixed with a single patch.
The researcher has pointed out the reasons for the discrepancy between these numbers:
- Some single reports included information about multiple problems, e.g. issue #2375 was addressed by four CVEs,
- Some groups of reports were fixed with a single patch, e.g. issues #2392 and #2408 as CVE-2023-23420,
- One bug report was closed as WontFix and not addressed in a security bulletin at all (issue #2508).
Microsoft met the Project Zero 90-day disclosure deadline for all reported vulnerabilities, with an average fix time of 81 days.
Jurczyk also submitted an additional 20 issues with low or unclear security impact to Microsoft between November 2023 and January 2024. These reports were sent without a disclosure deadline and later published on the Project Zero team's GitHub repository.
Microsoft fixed 6 of these issues in a security bulletin, while the remaining 14 were closed as "WontFix" with the possibility of being addressed in future Windows versions.
Multiple Windows version Affected
The discovered vulnerabilities affected various Windows platforms, including Windows 10, Windows 11, and Windows Server versions. The bugs impacted different attack targets, such as the kernel itself, drivers implementing registry callbacks, and privileged user-mode applications or services. The entry points for these vulnerabilities ranged from direct registry operations and hive loading to transaction log recovery.
Jurczyk performed a preliminary analysis of the exploitability of each bug, classifying them as either "easy," "moderate," or "hard" to exploit. The results showed that more than half of the findings could be feasibly exploited for information disclosure or local privilege escalation.
Many of the vulnerabilities exhibited registry-specific bug classes, enabling unique exploitation primitives. For example, hive-based memory corruption could be transformed into a KASLR bypass and a fully reliable arbitrary read/write capability, allowing a single bug to compromise the kernel with a data-only attack.
Developed PoC Exploits
To demonstrate the severity of these vulnerabilities, Jurczyk successfully developed exploits for CVE-2022-34707 and CVE-2023-23420, showcasing the potential for attackers to elevate privileges to SYSTEM on Windows 11.
The Windows Registry has a rich history, dating back to its introduction in Windows 3.1 in 1992. Since then, it has evolved significantly, with major changes occurring in Windows NT 3.1, Windows 95, and Windows NT 4.0.
The registry's binary format, known as "regf," has undergone several revisions, with version 1.3 introduced in Windows NT 4.0 still being supported in modern Windows versions.
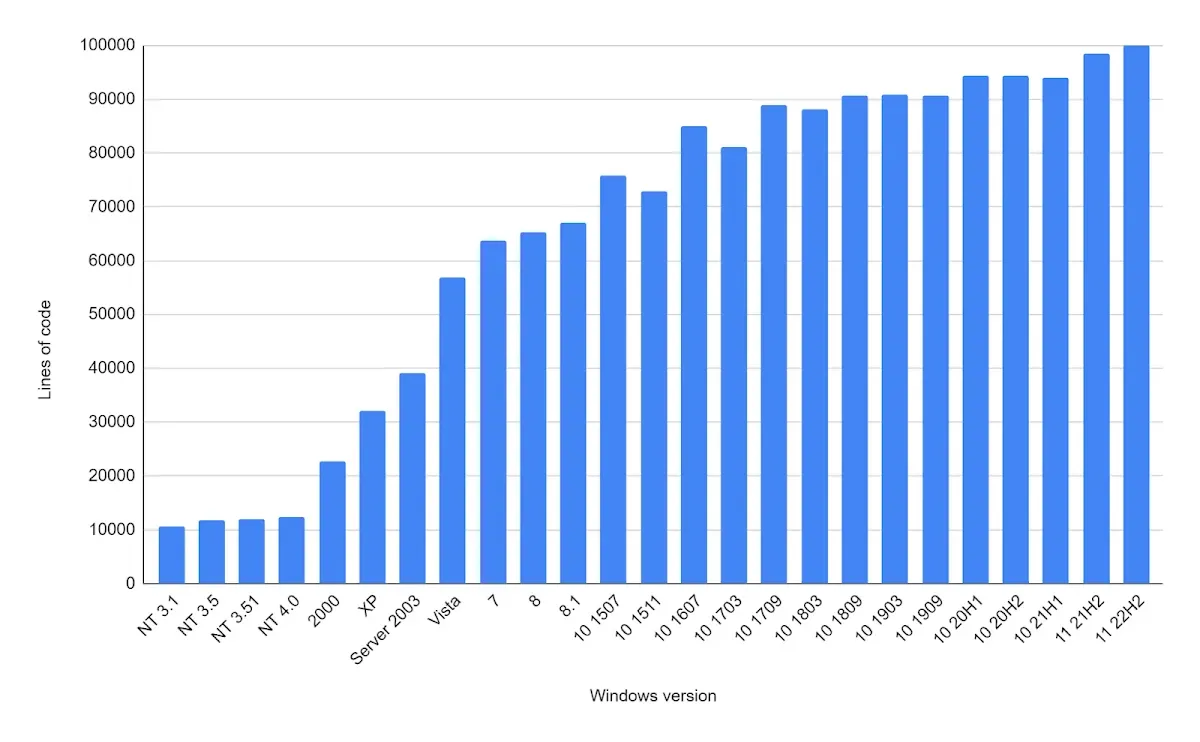
An analysis of the kernel-mode Configuration Manager code across various Windows versions reveals a tenfold increase in the number of lines of code, from approximately 10,000 in NT 4.0 to around 100,000 in Windows 11. This growth can be attributed to optimizations, backwards compatibility efforts, and the introduction of new features.
As the research was a 20-month audit, Jurczyk had already given a talk titled "Exploring the Windows Registry as a powerful LPE attack surface" at Microsoft BlueHat Redmond in October 2023.
You can also check the Jurczyk slides here.
As the Windows Registry continues to evolve and expand, Microsoft and the security community must remain vigilant in identifying and addressing potential vulnerabilities to ensure the safety and stability of Windows systems worldwide.

![Pirate Bay Proxy List 2024: Unblock The Pirate bay33 [April Updated]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjSLpBFGVKLEpg0rc9hECOaiGYOmFojg3gsCSrkKpqXYG0RxcBV7t3BFsdegN7e8J3UyclrJWT5N7mCzorsDb1hm66s6Pu91SJOEAQJxeodTlFuiPFEy77VIvaNZD2GlPf3jNlWLwhP8CS7WHCb9avIIPNAtdmVhoIXx3ybf26WAWInoDnBsp4aLtZ1/w250-h250-p-k-no-nu/The%20Pirate%20Bay%20proxies%202023.webp)




