A Security Researcher Stephen Sclafani has found a critical Security vulnerability on the Social network site Facebook, which allow him to hack any of Facebook users account and that also just by Users ID only. On the blog post Stephen, wrote that a mis-configured endpoint allowed legacy REST API calls to be made on behalf of any Facebook user using only their user ID.
Hope you all know that the users ID of any of the Facebook users account can be know through Graph API (http://graph.facebook.com/user name). And by this USER ID, Stephen can hack any of the Facebook acount even of Facebook Co-founder, Mark Zuckerberg.
What Attacker Can DO ?
With this hack Stephen can view private message, view private notes and drafts, view primary email address, make the status updates, upload photos, tag photos, likes or comment on any of the status or post, delete, edit any of the post or comments. And these all activity can be done without users interaction.
Explanation of the Research
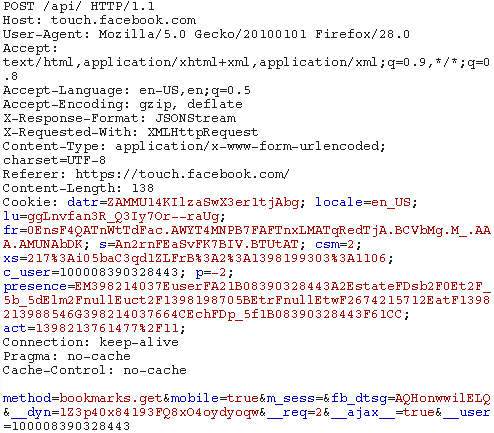
Stephen had started research with sending request with Facebook mobile site (touch.facebook.com), and he used Brup tool to intercept the request.
On the blog post he explained
The request was used to get your bookmarks. The request was interesting for three reasons: it was making an API call rather than a request to a dedicated endpoint for bookmarks; it was being made to a nonstandard API endpoint (i.e. not graph.facebook.com); the call was not Graph API or FQL. Doing a Google search for bookmarks.get turned up nothing. After some guessing I found that the method notes.get could also be called which returned your notes. Through some more searching I found that the endpoint was using Facebook’s deprecated REST API.
Facebook REST API was the predecessor of Facebook’s current Graph API, and Facebook have removed all the documents of REST API from the site, but researcher have managed to somehow collect all the API's documents from Way Back Machine - Researcher wrote,
Further more researcher proceed for Publishing method of Facebook and then he made another request,
Reseacher says Calling this method updated the status on the account that I was logged in to. The update was displayed as being made via the Facebook Mobile application.
This is an internal application used by the Facebook mobile website. Many internal Facebook applications are authorized and granted full permissions for every use- he added
Stephen had found this bug on April 23 and reported to Facebook team. Firstly Facebook have implement a temporary fix for this vulnerability but on April 30th Facebook team have permanently fixed the bug. For this bug Facebook rewarded $20,000 to Stephen as a part of their Bug Bounty Program.