One of the popular online banking platform Paypal have been hacked in a single click. The eBay owned company was vulnerable to a critical vulnerability which allows an attacker to take control on any of Paypal's users account with a single click.
A security researcher Yasser H. Ali from Egypt have discovered three critical security vulnerability in Paypal site which are Cross-Site Request Forgery (CSRF) , Resetting the security question and Auth token bypass. The vulnerabilities is raise to High as it lefts more than 150 million Paypal's users under threat.
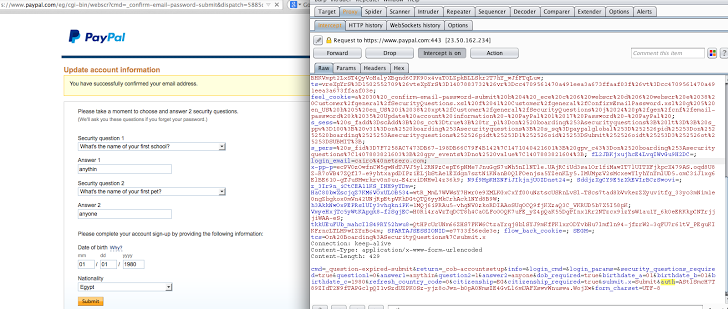
Researcher have posted a video demonstration of the of the vulnerability, where he explain how he had hacked Paypal's with a single click by its own exploit code. According to the demo, using Paypal CSRF exploit an attacker is able to secretly associate a new secondary email ID (attacker's email) to the victim's account, and also reset the answers of the security questions from target account.
In the reference of the security Paypal uses security Auth tokens for detecting the legitimate requests from the account holder, but Yasser had successfully bypassed the Auth tokens by the coded exploit.
How Exploits Works
For all three vulnerabilities Yasser have develop a single exploit which can exploit the CSRF vulnerability, bypassing the Auth tokens. Once the exploits execute, it add attacker's email id to victim's account, which is further used to change the passwords of victims accounts.
But as Paypal verifies the security question to change the account passwords, in this Yassir initially failed to change the victims passwords.
Later on he had found another bug in Paypal which allow him to reset the security questions and their answers of his choice. Finally, Yasser have successfully bypassed all the Paypal's security check and can took over any Paypal accounts.
The vulnerability has been fixed by the Paypal's team and Yasser was rewarded with $10,000 USD as a part of Paypal's bug bounty program. Earlier also Yasser had found a critical security vulnerability in eBay site which is used to hijack millions of user accounts in bulk.
A security researcher Yasser H. Ali from Egypt have discovered three critical security vulnerability in Paypal site which are Cross-Site Request Forgery (CSRF) , Resetting the security question and Auth token bypass. The vulnerabilities is raise to High as it lefts more than 150 million Paypal's users under threat.
How Exploits Works
For all three vulnerabilities Yasser have develop a single exploit which can exploit the CSRF vulnerability, bypassing the Auth tokens. Once the exploits execute, it add attacker's email id to victim's account, which is further used to change the passwords of victims accounts.
But as Paypal verifies the security question to change the account passwords, in this Yassir initially failed to change the victims passwords.
Later on he had found another bug in Paypal which allow him to reset the security questions and their answers of his choice. Finally, Yasser have successfully bypassed all the Paypal's security check and can took over any Paypal accounts.
The vulnerability has been fixed by the Paypal's team and Yasser was rewarded with $10,000 USD as a part of Paypal's bug bounty program. Earlier also Yasser had found a critical security vulnerability in eBay site which is used to hijack millions of user accounts in bulk.