World's most nitrous hackers group Team GhostShell - which are behind some major cyber attacks including attacks on the FBI, NASA and the Pentagon as well as a leak that saw 2.5 million Russian “government, educational, academic, political and law enforcement” accounts compromised, now came forward and gives its own identity.
GhostShell was most active in 2012, penetrating the aforementioned hacks on US and Russian intelligence agencies, but the silence that came in the three years between their last public attack and the subsequent return wasn’t quite the death of the group that many thought it would be.
GhostShell was most active in 2012, penetrating the aforementioned hacks on US and Russian intelligence agencies, but the silence that came in the three years between their last public attack and the subsequent return wasn’t quite the death of the group that many thought it would be.
G Razwan Eugen, was the man behind the Team GhostShell. Eugen came forward with a generic email address named White Fox that claimed to be the leader of the infamous hacker collective.
He contacted to TWN security writer Bryan Clark, and Clark joined some other security journalist of wired, telegraph on the discussions.
Without wasting a time all started discussions and verifying the claim (hacker). Verifying hackers is and always has been a tricky proposition. While it’s simple to verify that this person is a member of GhostShell, tying his true identity to that of a hacker pseudonym is infinitely more difficult.
Hackers, after all, are notoriously careful about keeping the two identities separate — OpSec mistakes in this crucial step are generally what lead to arrest.
Hackers, after all, are notoriously careful about keeping the two identities separate — OpSec mistakes in this crucial step are generally what lead to arrest.
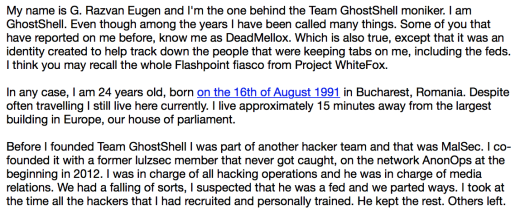
To prove the true identity, he wrote story on mail (check below image), and also provide couple of account login screenshots like Twitter and Pastebin.
 |
| Group Pastebin account |
 |
| Official Twitter account |
Twitter account was used by the official GhostShell Twitter account (@TeamGhostBin) to disseminate leaked information before its suspension.
As this is not enough to prove the true identity, hence we can't relay on this.
Eugen told Bryan-“I just want to own up to my actions, face them head on and hope for the best. What I really want is to continue being part of this industry. Cybersecurity is something that I enjoy to the fullest even with all the drama that it brings and legal troubles.
In return I hope other hackers and hacktivists take inspiration from this example and try to better themselves. Just because you’ve explored parts of the internet and protested about things that were important to you doesn’t mean you should be afraid and constantly paranoid of the people around you.”