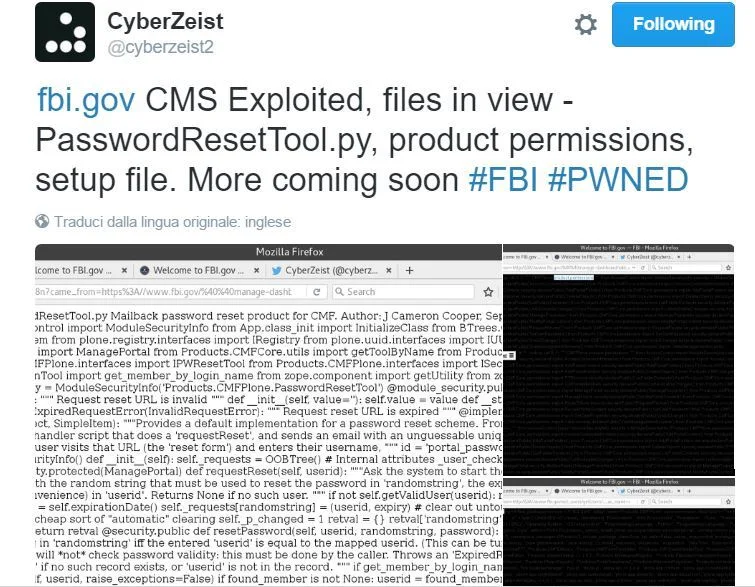
Earlier last week we had retweeted the tweet of a hacker having online handle (@cyberzeist2) that contains the 0day Vulnerability on FBI website. Now same hacker (cyberzeist2) have exploited the zero-day and gained some of the backup files from the server.
All the backup files data had been leaked online on pastebin.
The backup files contain the accounts data including names, password (SHA1 encrypted) and emails.
CyberZeist explained that he did not find the zero-day in CMS he exploited, he was just tasked to test it against the websites of the FBI and Amnesty.
At the meantime FBI are working on fix for the Vulnerability, he noticed that plone 0day exploit was still working against the CMS backend.
Hacker mentioned that he not published the zero-day exploit now as the Plone 0day is being out for sale on Tor by a hacker that goes by the moniker “lo4fer.” Once this 0day is no longer being sold, I will tweet out the Plone CMS 0day attack vector myself.
All the backup files data had been leaked online on pastebin.
The backup files contain the accounts data including names, password (SHA1 encrypted) and emails.
The Vulnerability was resides in some Python modules of the CMS. Other websites are potentially exposed to the same zero-day attack, including Intellectual Property Rights Coordination Center and EU Agency for Network Information and Security.
Cyberzeist2 had already posted a photo showing the Vulnerability on last year December 22, but then also FBI team have not contacted him at time -says hacker.
“I was contacted by various sources to pass on the leaks to them that I obtained after hacking FBI.GOV but I denied all of them. Why? just because I was waiting for FBI toThere was very silly mistakes done by developer as he/she had put the backup files on same server, which makes hacker works very easy.
react on time. They didn’t directly react and I don’t know yet what are they up to, but at the time I was extracting my finds after hacking FBI.GOV,” he wrote.
“I couldn’t gain a root access (obviously!), but I was able to recon that they were running FreeBSD ver 6.2-RELEASE that dates back to 2007 with their own custom configurations. Their last reboot time was 15th December 2016 at 6:32 PM in the evening.” he added.
Hacker mentioned that he not published the zero-day exploit now as the Plone 0day is being out for sale on Tor by a hacker that goes by the moniker “lo4fer.” Once this 0day is no longer being sold, I will tweet out the Plone CMS 0day attack vector myself.