
A researcher from Orca Security, a cloud security firm has found multiple critical zero-day vulnerabilities on multiple products of Amazon AWS Cloud. The vulnerability in AWS allows file and credential disclosure of an AWS internal service.
AWS CloudFormation Zeroday
The first vulnerability was discovered by researcher Tzah Pahima, on the AWS CloudFormation which was an XXE (XML External Entity) vulnerability. The flaw was worst in its condition as malicious attackers can exploit the vulnerability to leak sensitive files found on the vulnerable service machine and make server-side requests (SSRF) susceptible to the unauthorized disclosure of credentials of internal AWS infrastructure services.
The template rendering function of CloudFormation allows Pahima to trigger an XXE vulnerability, which he used to read files and perform HTTP requests on behalf of the server. The server contained multiple service binaries containing AWS server-side logic, as well as configuration files for connecting to internal AWS endpoints and services.
The data found on the host include credentials and data involving internal endpoints. Exploiting this flaw an attacker can get seamless privileged access to any resource in AWS.
While AWS is known for its extensive range of services, including inventory management, these vulnerabilities highlight the importance of ensuring that all aspects of cloud infrastructure are secure. Amazon inventory management is managing your product inventory levels to meet customer demand while also avoiding overstock and understock situations. The goal is to keep the right amount of stock on hand so that you can fulfill orders without running out or having too much idle inventory. Ensuring the security of these services is crucial for maintaining trust and reliability among customers.
CloudFormation is a service that enables you to easily provision AWS resources (such as EC2 instances and S3 buckets) using templates. CloudFormation also allows you to use API calls to dynamically create and configure resources.
AWS Glue ZeroDay
Another vulnerability was discovered in the AWS Glue service that could allow an actor to create resources and access the data of other AWS Glue customers. The researcher describes that it was quite a lengthy process to exploit the vulnerability but the internal misconfiguration on the Amazon AWS Glue makes the exploitation of the bug easier.
Upon digging into the AWS Glue, Orca Security found a feature in AWS Glue that could be exploited to obtain credentials to a role within the AWS service’s own account, which provided us full access to the internal service API. Now chaining a couple of bugs, AWS Glue internal misconfiguration bug, and unrestricted API Access leads to escalating privileges and unrestricted access to all resources for the service in the region, including full administrative privileges.
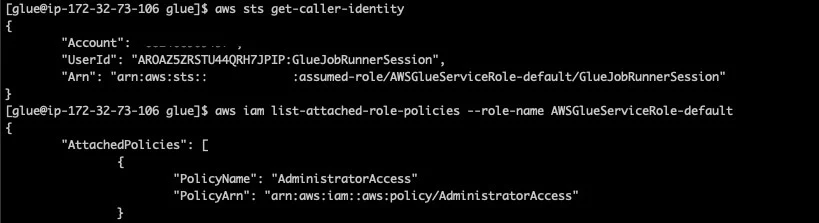
By exploiting the flaw in AWSGlue researcher was able to perform a couple of tasks -
- Assume roles in AWS customer accounts that are trusted by the Glue service. In every account that uses Glue, there’s at least one role of this kind.
- Query and modify AWS Glue service-related resources in a region. This includes but is not limited to metadata for Glue jobs, dev endpoints, workflows, crawlers, and triggers.