Researchers from FingerprintJS, a Chicago-based Software development firm identified a user data-leaking vulnerability in Apple's web browser including iOS and iPadOS web browsers. Actually, the flaws reside in the IndexDB API that violates the same-origin policy.
In Safari 15 on macOS, and in all browsers on iOS and iPadOS 15, every time a website interacts with a database, a new (empty) database with the same name is created in all other active frames, tabs, and windows within the same browser session.
This is a violation of the same-origin policy's fundamental security mechanism that restricts how documents or scripts loaded from one origin can interact with resources from other origins. An origin is defined by the scheme (protocol), hostname (domain), and port of the URL used to access it.
IndexedDB is a browser API for client-side storage designed to hold significant amounts of data. It’s supported in all major browsers and is very commonly used. As IndexedDB is a low-level API, many developers choose to use wrappers that abstract most of the technicalities and provide an easier-to-use, more developer-friendly API.
How this Leak is Bad?
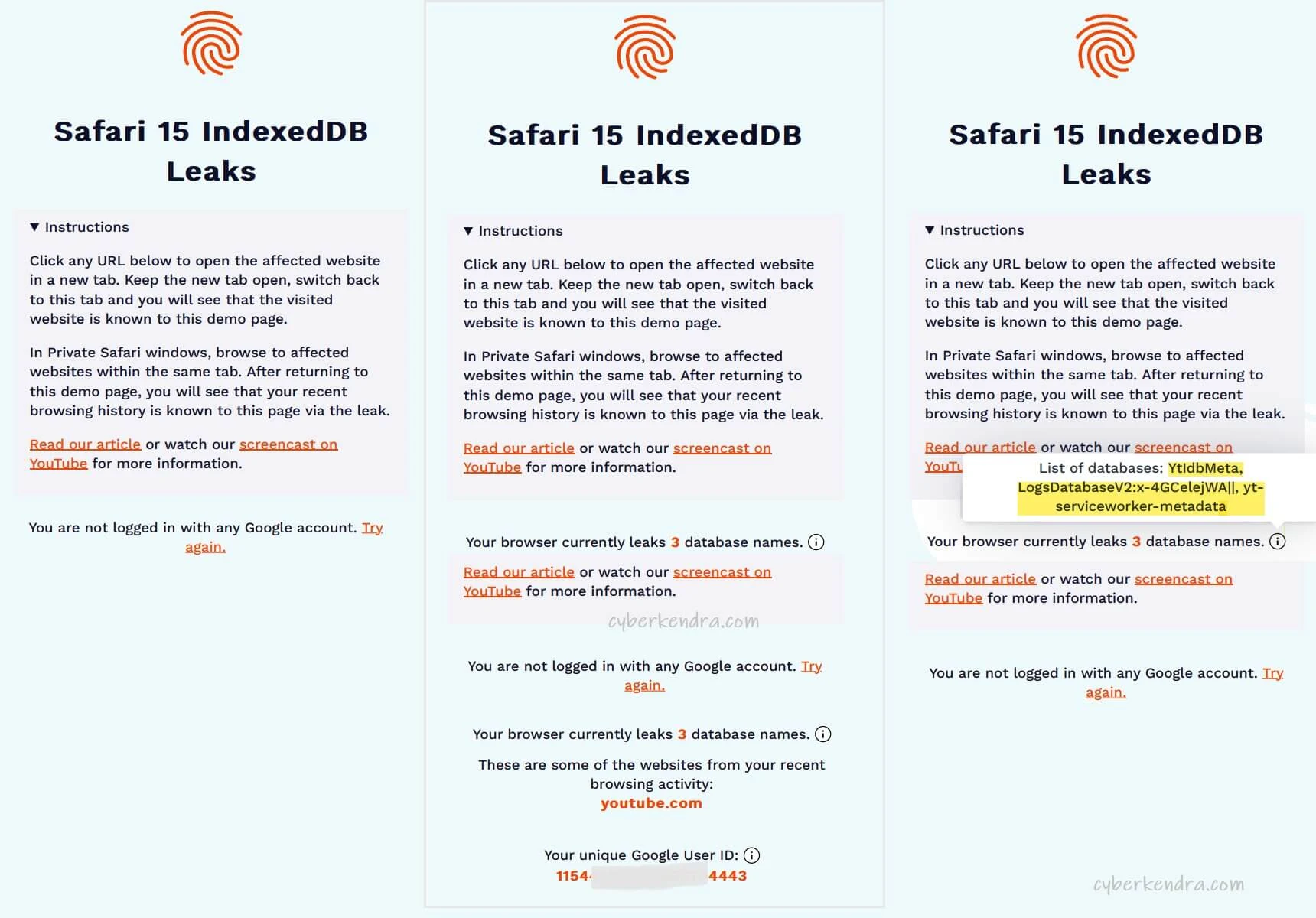
As IndexDB leaks database names across different origins which is surely a privacy violation, it lets arbitrary websites learn what websites the user visits in different tabs or windows. On the blogpost FingerprintJS noted-
"We observed that in some cases, websites use unique user-specific identifiers in database names. This means that authenticated users can be uniquely and precisely identified. Some popular examples would be YouTube, Google Calendar, or Google Keep. All of these websites create databases that include the authenticated Google User ID and in case the user is logged into multiple accounts, databases are created for all these accounts."
"The Google User ID is an internal identifier generated by Google. It uniquely identifies a single Google account. It can be used with Google APIs to fetch the public personal information of the account owner." - further added.
This flaw is critical as this discloses user privacy, which doesn't require any specific user action A tab or window that runs in the background and continually queries the IndexedDB API for available databases, can learn what other websites a user visits in real-time. Alternatively, websites can open any website in an iframe or popup window in order to trigger an IndexedDB-based leak for that specific site.
Safari Private Mode is not also not Safe.
As the vulnerability is from the same-origin policy of IndexDB API, the same-origin policy is an effective security mechanism for all window modes, so this even affects Safari Private Mode.
Websites with one origin should never have access to resources from other origins regardless of whether a visitor is using private browsing or not unless it’s explicitly allowed via cross-origin resource sharing (CORS).
But it’s important to note that browsing sessions in private Safari windows are restricted to a single tab, which reduces the extent of information available via the leak. However, if you visit multiple different websites within the same tab, all databases these websites interact with are leaked to all subsequently visited websites.
Proof & Video Demonstration
For the PoC of the flaw, the FingerprintJS team has published a video demonstrating the workflow of the bug by showing leak datasets. They have also published a website that shows the demonstration of flaws.