Update: (scroll below)
7. The Okta contractor, Sykes, has confirmed a breach of “parts” of their network in January.
6. Okta Official Statement and Lapsus Group counter statement.
5. Cloudflare security advisory with guides to Okta customers.
4. Okta CEO statement regarding the hack claims.
3. Cloudflare's founder statement with precations steps.
2. A leaked screenshot shows the date as 21st January, Lapsus hacker group confirmed that they were accessing the Okta since January.
1. Okta is aware of the report and is currently investigating the breach incident.
Also Read:
- Seven Teenagers Arrested in Connection with Lapsus$ Hacker Group
- Microsoft confirms Lapsus$ compromised "a single account" with "limited access" and exfiltrated portions of source code for some of its products.
- A Teenager Reportedly Behind the Lapsus$ Hacking Group.
Just an hour after publishing Microsoft Bing, Bing Maps, and Cortana Source code along with the LG.com employee accounts details, the Lapsus$ hacker group has just published another batch of evidence new breach of the Okta system.
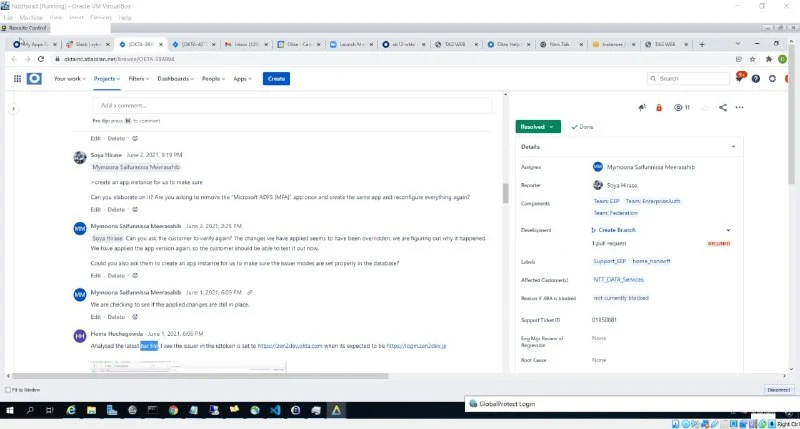
Lapsus group shared multiple screenshots of accessing the Okta service and gained Superuser/Admin. Okta is an access management company based in San Francisco. It provides cloud software that helps companies manage and secure user authentication into applications, and for developers to build identity controls into applications, website web services, and devices.
Below here are the screenshots of accessing Okta services. (Click Image to Enlarge)
.jpeg)



.jpeg)


According to the above screenshot, Lapsus had access to the Superuser account of Okta which also had used AWS, Okta Superuser, Zoom app, Okta Sales, Atlassian Cloud Jira & Confluence, Cornerstone (Okta learning portal), Gmail, Crayon and Splunk, etc app.
From the Cloudflare screenshot, it seems that users whose account was hacked were naming, Alex Stirbu. Lapsus has also shared the System Log Event log of the Okta service. Furthermore, they have also tried to reset the user's account password.
Lapsus hacker mentioned that they haven't stolen or accessed any data from Okta. Their message reads-
BEFORE PEOPLE START ASKING: WE DID NOT ACCESS/STEAL ANY DATABASES FROM OKTA - our focus was ONLY on okta customers.
Updates:
Okta Investigating the Hack Incident
Authentication service provider Okta says they are aware of the reports and were investigating the breach incident. Okta official said in the brief statement -
"We will provide updates as more information becomes available"
If this hack comes true, it could have major consequences because thousands of other organizations/companies depend on Okta to manage access to their own networks and web applications.
Cloudflare Advisory, Resetting Password
Cloudflare's founder confirmed that there is no evidence that Cloudflare has been compromised. For security precautions, Cloudflare is resetting the Okta credential of any employees who have changed their passwords in the last 4 months.
[update] Now, Cloudflare has released the advisory regarding the hacking incident. On the blogpost, Cloudflare has detailed the steps taken after their name and employee's details came up on screenshots shared by the Lapsus group. Cloudflare started investigating the incident and reviewed for potential suspicious activities, including password resets over the past three months. Even they suspend all accounts of users that could have been affected.
We use Okta internally for employee identity as part of our authentication stack. We have investigated this compromise carefully and do not believe we have been compromised as a result. We do not use Okta for customer accounts; customers do not need to take any action unless they themselves use Okta.- Cloudflare says.
What to do if you are an Okta customer
If you are also an Okta customer, you should reach out to them for further information. We advise the following actions:
- Enable MFA for all user accounts. Passwords alone do not offer the necessary level of protection against attacks. We strongly recommend the usage of hard keys, as other methods of MFA can be vulnerable to phishing attacks.
- Investigate and respond:
- Check all password and MFA changes for your Okta instances.
- Pay special attention to support initiated events.
- Make sure all password resets are valid or just assume they are all under suspicion and force a new password reset.
- If you find any suspicious MFA-related events, make sure only valid MFA keys are present in the user's account configuration.
- Make sure you have other security layers to provide extra security in case one of them fails.
Okta Official statement for Hack Incident

Finally, Okta Co-founder and CEO Todd McKinnon came up with the statement regarding the hack claims by the Lapsus group. McKinnon says-
Okta detected an attempt to compromise the account of a third-party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor.
We believe the screenshots shared online are connected to this January event. Based on our investigation to date, there is no evidence of ongoing malicious activity beyond the activity detected in January.
Okta Official Statement vs Lapsus counter words

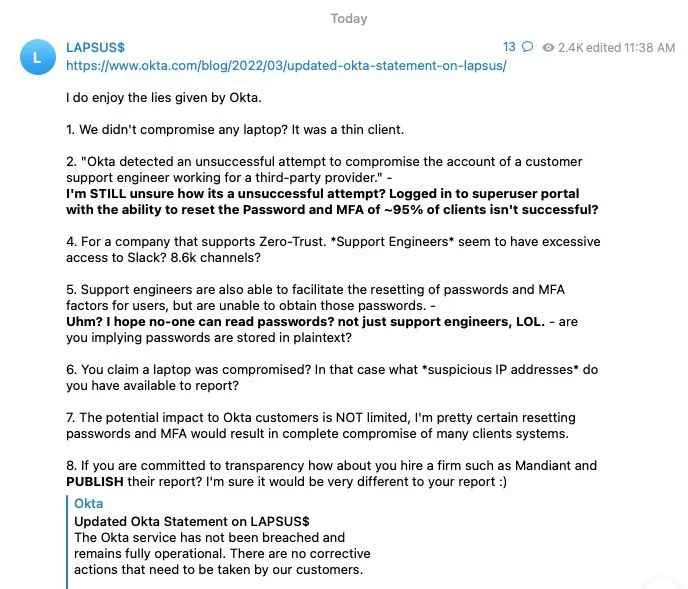
The Okta contractor, Sykes, has confirmed a breach
The support provider targeted by the hackers, according to the screenshots provided by LAPSUS$ on its Telegram group, is Sykes Enterprises, which is contracted by Okta for customer services from Costa Rica. The company, part of the Sitel Group, told Forbes that “parts of the Sykes network,” had been breached in January, and “we took swift action to contain the incident and to protect any potentially impacted clients.
“Further to the actions taken by our global security and technology teams, a worldwide cybersecurity leader was enlisted to conduct an immediate and comprehensive investigation of the matter. Following completion of the initial investigation, working in partnership with the worldwide cybersecurity leader, we continue to investigate and assess potential security risks to both our infrastructure and to the brands we support around the globe,” the spokesperson said.