
According to GitHub, the first vulnerability, CVE-2022-24765 affects users working on multi-user machines where untrusted users can create a C:\.git\config (on Windows system) directory which would be picked up by Git operations run supposedly outside a repository while searching for a Git directory.
"Since some configuration variables (such as core.fsmonitor) cause Git to execute arbitrary commands, this can lead to arbitrary command execution when working on a shared machine." Github security engineer Taylor Blau noted.
Who are Vulnerable
According to the security advisory, users
- who installed posh-git are vulnerable simply by starting a PowerShell
- Git Bash users who set GIT_PS1_SHOWDIRTYSTATE are also vulnerable.
- Users of IDEs such as Visual Studio are vulnerable: simply creating a new project would already read and respect the config specified in C:\.git\config.
- Users of the Microsoft fork of Git are vulnerable simply by starting a Git Bash.
"the default system settings for TMP and TEMP are to point to C:\Windows\Temp, a folder that is world-writable (for historical reasons), and the SYSTEM user account inherits those settings. This means that any authenticated user can place malicious .dll files that are loaded when Git for Windows' uninstaller is run via the SYSTEM account." - the advisory reads.
It is to be noted that GitHub is unaffected by these vulnerabilities. However, users should be aware of these vulnerabilities and upgrade their local installation of Git, especially if users are using Git for Windows, or you use Git on a multi-user machine.
Mitigation
Both the above vulnerabilities have been fixed in the latest version of Git, so it is highly recommended to upgrade to Git v2.35.2. This version changes Git’s behavior when looking for a top-level .git directory to stop when its directory traversal changes ownership from the current user. If you wish to make an exception to this behavior, you can use the new multi-valued safe.directory configuration.
If you can't upgrade your Git right now [for any reason], you can follow the below steps to reduce the risk.
For vulnerability CVE-2022-24765,
- Define the GIT_CEILING_DIRECTORIES environment variable to contain the parent directory of your user profile (i.e., /Users on macOS, /home on Linux, and C:\Users on Windows).
- Avoid running Git on multi-user machines when your current working directory is not within a trusted repository.
- Avoid running the uninstaller until after upgrading
- Override the SYSTEM user’s TMP environment variable to a directory which can only be written to by the SYSTEM user
- Remove unknown .dll files from C:\Windows\Temp before running the
- uninstaller
- Run the uninstaller under an administrator account rather than as the
- SYSTEM user
NotGitBleed: Credentials Leaks on GitHub and Other Datastores
.webp)
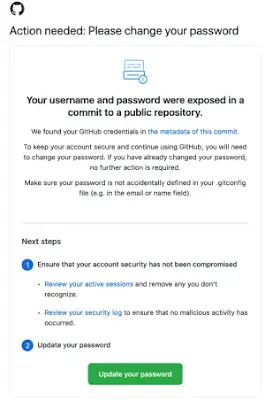
In the blog post, GitHub says that it will scan public repositories for accidentally leaked GitHub login credentials, to prevent attackers from finding these. If a user accidentally exposes their username and password in code or commits metadata, GitHub will automatically reset their password and inform them via email.
Will Deane, Director and Principal Consultant at ASX Consulting, and Aaron Devaney, Principal Security Consultant at MDSec, have uncovered the threat of exposed passwords in GitHub. We have already written about their research named "NotGitBleed".