
Atlassian has released security updates to address three critical-severity vulnerabilities in its products that could be exploited to cause an authentication bypass or cross-site scripting and take control of affected systems.
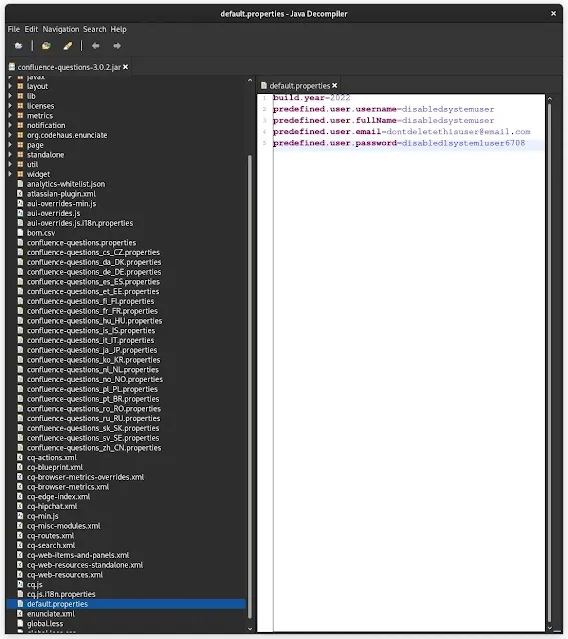
The first of the three flaws, CVE-2022-26138 (CVSS score: 8.6), affects Confluence Server and Data Center products, and, allows a remote, unauthenticated attacker with knowledge of the hardcoded password. The hardcoded password is added after installing the Questions for Confluence app (versions 2.7.34, 2.7.35, and 3.0.2) for a user account with the username disabledsystemuser — designed to help admins with the migration of data from the app to the Confluence Cloud.
When the Questions for Confluence app is enabled on Confluence Server or Data Center, it creates a Confluence user account with the username disabledsystemuser. This account is intended to aid administrators that are migrating data from the app to Confluence Cloud. The disabledsystemuser account is created with a hardcoded password and is added to the confluence-users group, which allows viewing and editing all non-restricted pages within Confluence by default. A remote, unauthenticated attacker with knowledge of the hardcoded password could exploit this to log into Confluence and access any pages the confluence-users group has access to.
According to Atlassian, the app helps improve communication with the organization's internal Q&A team and is currently installed on over 8,000 Confluence servers. Atlassian noted the issue has not been exploited in the wild, as the hardcoded password is trivial to obtain after downloading and reviewing affected versions of the app.
Verify Your Instances for Affected version
| Affected App | Affected Version |
|---|---|
| Questions for Confluence 2.7.x |
|
| Questions for Confluence 3.0.x | 3.0.2 |
If you want to determine whether your Confluence Server or Data Center instance is affected or not then check it with the below credential if it has an active user account or not —
- User: disabledsystemuser
- Username: disabledsystemuser
- Email: [email protected]
 |
| image: @fluepke |
If this account does not show up in the list of active users, the Confluence instance is not affected.
How To Look For Evidence of Exploitation
Firstly server admin can search for the disabledsystemuser account and either disable it or delete it. To disable or delete the account, you can use the detailed steps provided in this support document.
To determine if anyone has successfully logged in to the disabledsystemuser account, refer to this support document page, which provides instructions on how to get a list of users' last logon times. If the last authentication time for disabledsystemuser is null, that means the account exists but no one has ever logged into it.