
The flaw has been demonstrated by Patrick Wardle at the Def Con hacking conference in Las Vegas showing a privilege escalation attack gaining root access over the Mac operating system. The exploit works by targeting the installer for the Zoom application, which needs to run with special user permissions to install or remove the main Zoom application from a computer.
According to Wardle initially, the installer requires a user to enter their password on adding the application to the system but later Wardle found that an auto-update function then continually ran in the background with superuser privileges. When Zoom issued an update, the updater function automatically installs the new package or update after checking that it had been cryptographically signed by Zoom.
In his research, he found a bug in how the checking method was implemented meant that giving the updater any file with the same name as Zoom's signing certificate would be enough to pass the test, so an attacker could substitute any malware program and have it be run by the updater with elevated privilege.
Attacker Needs Initial Access to the System
For the exploitation of the bug, the attacker already needs to gain initial access to the target system and then employs an exploit to gain a higher level of access.
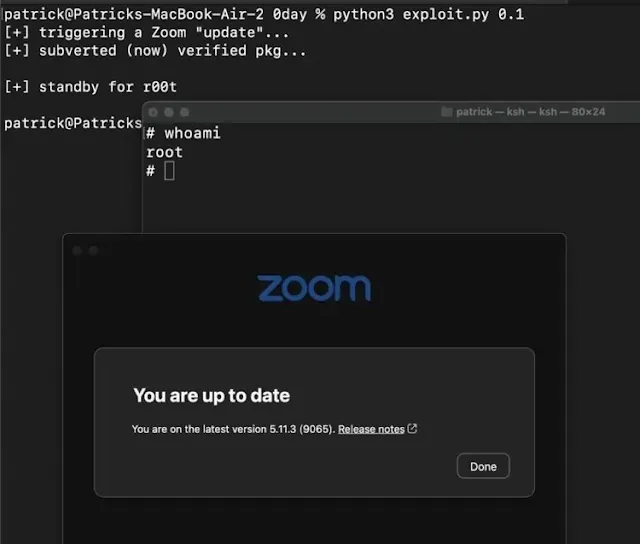 |
| Root access on Mac via the Zoom update feature |
The flaw has been reported by Wardle to the Zoom security team, but weeks before the Def Con event, Wardle says Zoom issued a patch that fixed the bugs that he had initially discovered. But on closer analysis, another small error meant the bug was still exploitable.
Zoom Released Fix
Zoom has released a new version of its macOS app with a fix for a security vulnerability affecting the app's automatic updates feature. The issue has been assigned CVE-2022-28756.
Zoom said version 5.7.3 to version 5.11.3 of its macOS app contains a vulnerability in the auto-update process that can be exploited by a local low-privileged user to gain root privileges to the operating system. The vulnerability has been patched in version 5.11.5 of the Zoom app for macOS, available now.
Update:18 August, Bypass of the patch
Another macOS Security researcher Csaba Fitzl @theevilbit has managed to bypass the fix implemented by the Zoom team. The bypass has been assigned CVE-2022-28757, allowing for a bypass of the patch issued in 5.11.5 to address CVE-2022-28756. So users are recommended to update the Zoom app to version 5.11.6.