
- Uber official statement.
Uber suffered a data breach in which hackers accessed the company's internal system including Uber AWS, GSuite,vSphere, domain admin accounts along with Hackerone staff accounts.
After the notification of the breach, Uber took off several of its internal communications and engineering systems offline along with access to the internal Slack messaging. The company tweeted the following statement regarding the hacking incident -
We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available.
The breach appeared to have compromised many of Uber’s internal systems, and a person claiming responsibility for the hack sent images of the email, cloud storage, and code repositories to cybersecurity researchers and The New York Times.
A security researcher Sam Curry says this attacker claimed to have completely compromised Uber. He also shared the screenshot of the hackerone bug report which shows hackers have also compromised Uber's HackerOne staff account.

Uber Investigating the breach Incident
Uber noted that they are investigating the breach incident and also communicating with the law enforcement agency.
In the meantime, Uber employees were instructed not to use the company’s internal messaging service, Slack, and found that other internal systems were inaccessible, New York Times reported. Shortly before the Slack system was taken offline on Thursday afternoon, Uber employees received a message that read, “I announce I am a hacker and Uber has suffered a data breach.”
Hacker Leaked Login Details and POC
Hacker has shared the screenshot showing access to the Uber Corp and other Cloud accounts with one of the security researchers.
Furthermore, Hackers also shared the login details of the Uber internal system and API keys of Uber Active Directory, Uber Corp credentials, OneLogin, VMWARE, and more...


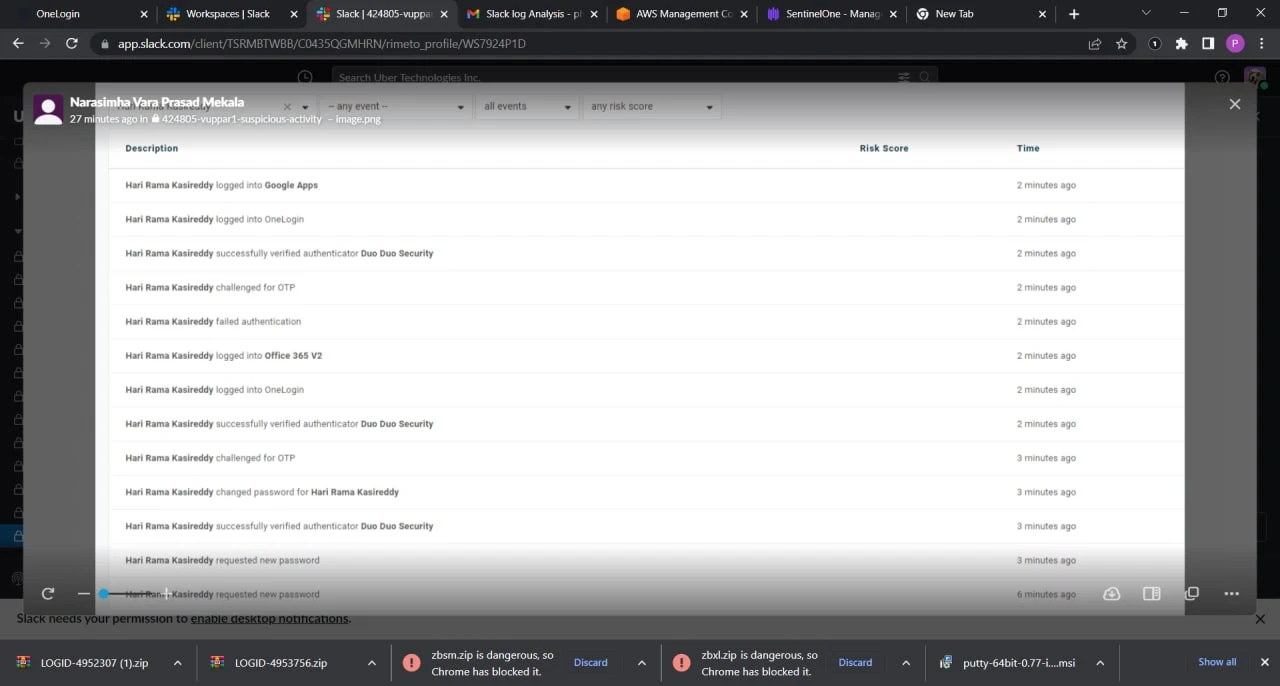
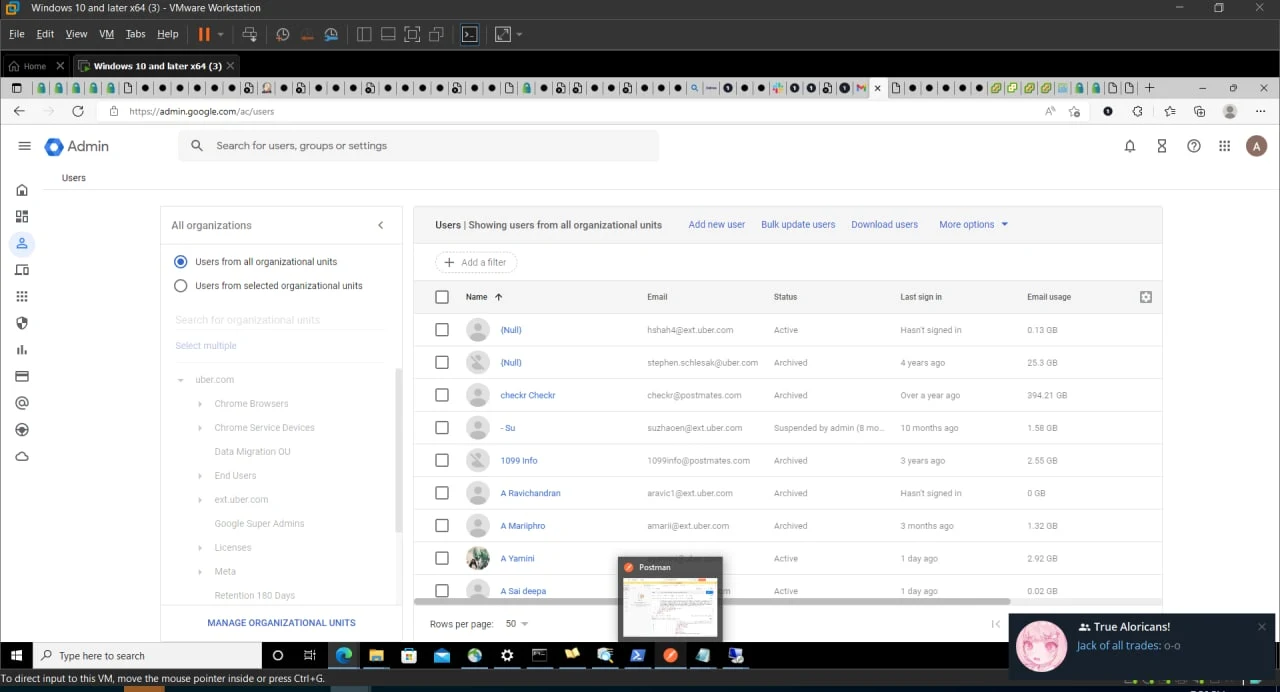
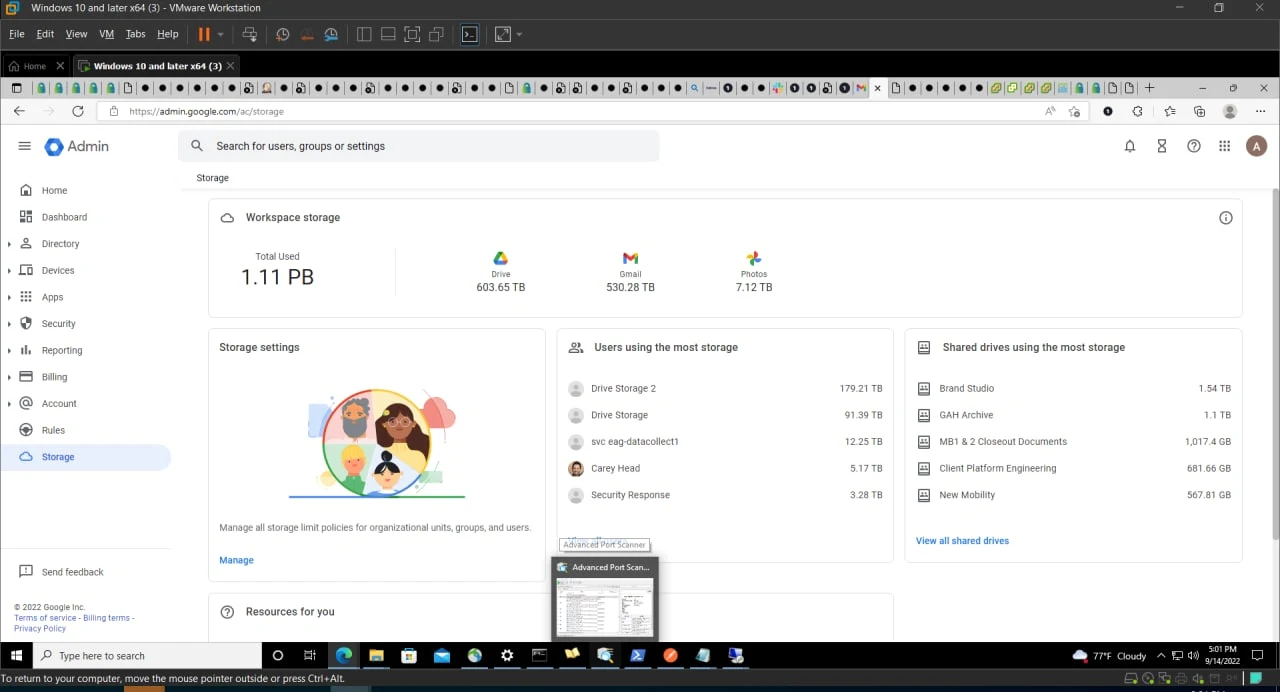


For security concerns, we are not sharing the link of the login details leaked by hackers.
[Update] Uber Official Statement
Finally Uber has come up with a statement regarding the breach incident stating that they didn't have any evidence that the incident involved access to sensitive user data (like trip history).
Additionally, the company is getting back all the Internal application tools that were taken down as a precautionary measure.
How was Uber hacked?
The hacker who claimed responsibility for the hack told NYTimes that he had sent a text message to an Uber worker claiming to be a corporate information technology person. The worker was persuaded to hand over a password that allowed the hacker to gain access to Uber’s systems, a technique known as social engineering.
Smishing is when scammers send text messages pretending to be from trusted sources. The goal is to get targets to respond with personal information like passwords and credit card details or to click on links that install malware. It is just like phishing that uses emails; instead, smishing uses texts.
It was not the first time that a hacker had stolen data from Uber. In 2016, hackers stole information from 57 million driver and rider accounts and then approached Uber and demanded $100,000 to delete their copy of the data. Uber arranged the payment but kept the breach a secret for more than a year.