
New spyware with hacking capabilities similar to NSO Group’s Pegasus has been discovered by security experts.
The spyware, which is marketed by an Israeli company called QuaDream, has already been used by clients to target journalists, political opposition figures, and an employee of an NGO.
Victims’ phones were infected with the spyware by receiving an iCloud calendar invitation from operators of the spyware, who are believed to be government clients. The attacks occurred between 2019 and 2021, and the hacking tool is marketed under the name Reign.
Like Pegasus, Reign allows a phone infected with it to record conversations near the phone, read messages on encrypted apps, listen to phone conversations, track a user’s location, and generate two-factor authentication codes on an iPhone to infiltrate a user’s iCloud account.
The new revelations mark another blow to Apple, which has marketed its security features as among the best in the world. Reign appears to be a unique and potent threat to the integrity of the company’s mobile phones.
How QuaDream's Spyware Works
The spyware developed by QuaDream infects iPhones by sending an iCloud calendar invitation to mobile users from operators of the spyware, who are likely to be government clients. Victims were not notified of the calendar invitations because they were sent for events logged in the past, making them invisible to the targets of the hacking.
Such attacks are known as “zero-click” because users of the mobile phone do not have to click on any malicious link or take any action to be infected.
Once infected, the spyware can record conversations that happen in the proximity of the phone by controlling the phone’s recorder, reading messages on encrypted apps, listening to phone conversations, and tracking a user’s location.
The spyware can also generate two-factor authentication codes on an iPhone to infiltrate a user’s iCloud account, allowing the spyware operator to exfiltrate data directly from the user’s iCloud.
QuaDream's Low Public Profile
Unlike NSO Group, QuaDream has a relatively low public profile. The company does not have a website or list other contact details. Israeli lawyer Vibeke Dank, whose email was listed on QuaDream's corporate registration form, did not return a message seeking comment.
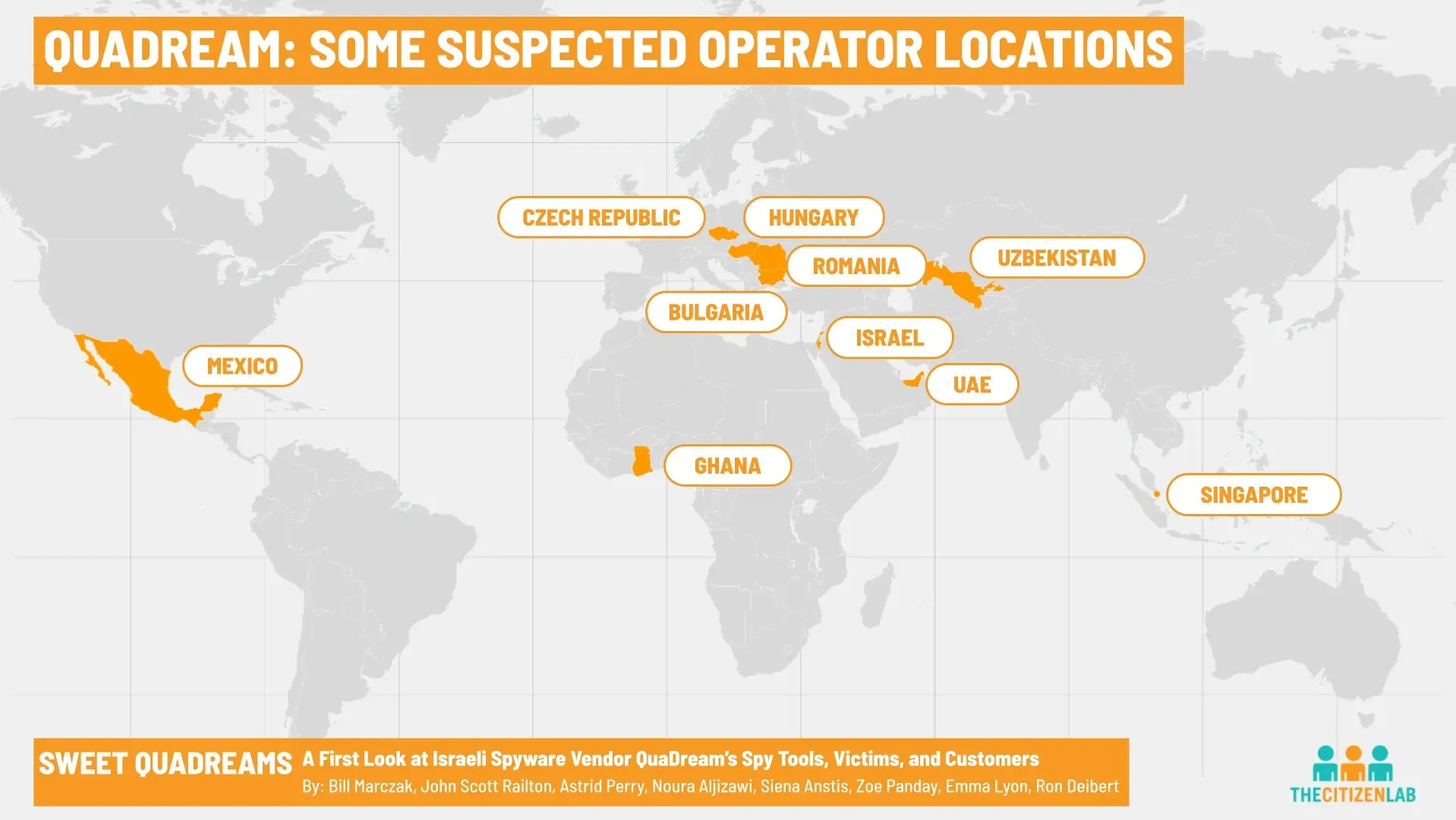 |
| Suspected locations of QuaDream operators. (img: Citizen Lab) |
Citizen Lab did not name the individuals who were found to have been targeted by clients using Reign, but it said that more than five victims – described as journalists, political opposition figures, and one employee of an NGO – were located in North America, Central Asia, south-east Asia, Europe, and the Middle East. Citizen Lab also said it was able to detect operator locations for the spyware in Bulgaria, the Czech Republic, Hungary, Ghana, Israel, Mexico, Romania, Singapore, the UAE, and Uzbekistan.
The company’s name was briefly referenced in a December 2022 security report issued by Meta, the parent company of Facebook, which described QuaDream as an Israeli-based company founded by former NSO employees.
At the time, Meta said it had removed 250 accounts on Facebook and Instagram that were linked to QuaDream and that it believed the accounts were being used to test the spyware maker’s capabilities using fake accounts, including exfiltrating data such as messages, images, video and audio files.
The discovery of Reign highlights the continued proliferation of highly sophisticated hacking tools, even as NSO Group, the maker of one of the world’s most sophisticated cyberweapons, has faced intense scrutiny and been blacklisted by the Biden administration, probably curtailing its access to new customers.