
In a recent disclosure by Ivanti, a leading IT service management solutions provider, two zero-day vulnerabilities in their products have been actively exploited, posing a serious threat to organizations.
The vulnerabilities, affecting Ivanti Connect Secure (ICS) and Policy Secure gateways, were disclosed without a patch, leaving customers vulnerable to potential cyber attacks.
Mandiant's threat intel team suggests that the identified vulnerabilities are CVE-2023-46805, an authentication bypass bug, and CVE-2024-21887, a command injection vulnerability, which has been under attack by cyberspies since December.
What makes these vulnerabilities particularly alarming is the fact that neither flaw has a patch and they can be chained together to achieve unauthenticated remote code execution, providing attackers the ability to take control of an organization's Ivanti network appliances and potentially infiltrate their IT environment.
Mandiant Consulting CTO Charles Carmakal highlighted the severity of the situation, emphasizing that the vulnerabilities pose a serious risk to organizations. As of now, Ivanti has acknowledged "less than 20 customers impacted by the vulnerabilities," the number of victims is expected to increase as more organizations identify compromised devices using Ivanti's integrity checking tool.
The company aims to release patches starting the week of January 22 in a staggered fashion. In the meantime, customers are strongly advised to deploy mitigations immediately to reduce the risk of exploitation.
Mandiant has been actively working with Ivanti to investigate and address the situation. Their initial analysis revealed that a previously unknown suspected espionage team, tracked as UNC5221, had been exploiting these vulnerabilities as early as December. The attackers primarily used hijacked end-of-life Cyberoam VPN appliances as command-and-control servers, which were domestic to the victims, aiding the threat actor in evading detection.
Earlier reports by Volexity which discovered the zero-day holes and privately reported them to Ivanti, linked the attackers to China. Mandiant refrains from making any attributions, citing insufficient data. The attacks were targeted and sophisticated, indicating a planned effort to maintain a presence on high-priority targets even after a patch was released.
Mandiant's investigation identified five custom malware families used by UNC5221 to exploit the Ivanti flaws.
- Zipline - A backdoor for command execution, file transfers, proxy access, and tunnelling.
- Thinspool - Used as an initial dropper for Lightwire webshell.
- Lightwire - Webshell for persistent access on compromised devices.
- Wirefire - Webshell stashed on Connect Secure appliances for remote control.
- Warpwire - Credential harvester to steal passwords for further network access.
In response to the threat, Mandiant has shared indicators of compromise, providing organizations with crucial information to detect and mitigate potential risks.
As the investigation unfolds, additional details will be provided to enhance understanding and preparedness against these cyber threats.
Identifying, Reproducing and POC
A cybersecurity firm, WatchTowr claims they have successfully reproduced both both in-the-wild exploited Ivanti zero-days (CVE-2023-46805 & CVE-2024-21887).
WatchTowr shared some of the basic information on reproducing the flaws with the POC image.
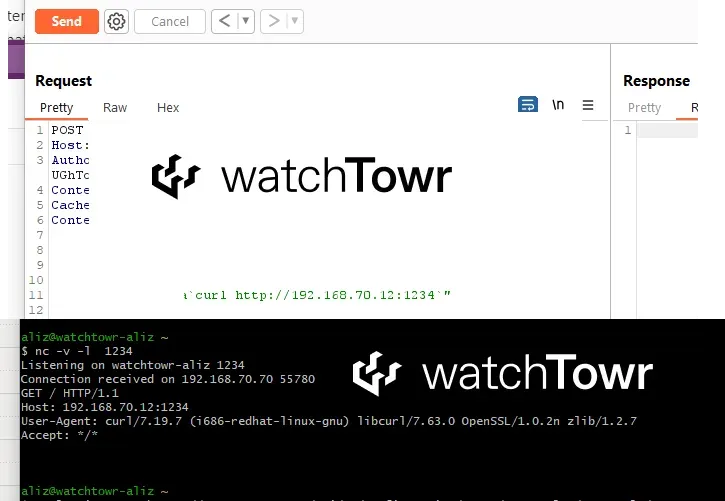 |
| Image: WatchTowr |
WatchTowr mentioned that they can't share the full details as both the bugs are in-the-wild exploitation, and Ivanti has not even released a patch. Sharing the details at this point is 'irresponsible'.
With the details shared by WatchTowr, a user 'Dhiraj' (@RandomDhiraj) has written an NMAP NSE script to check CVE-2023-46805 & CVE-2024-21887, which you can find on his GitHub repo.
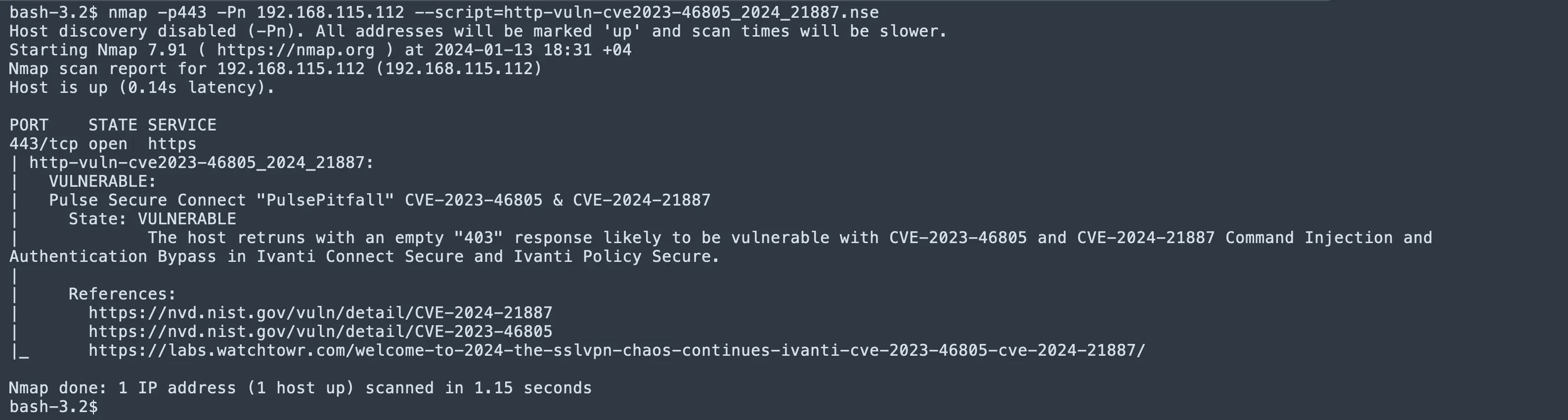 |
| Image: @RandomDhiraj |
Organizations using Ivanti products are urged to stay vigilant, apply mitigations promptly, and follow recommended security practices.
The collaborative efforts between Ivanti and Mandiant underscore the importance of industry cooperation in addressing and mitigating such critical cybersecurity incidents. As the situation evolves, staying informed and proactive remains crucial in safeguarding against potential cyber threats.