
A recent report from cyber intelligence firm Resecurity has revealed that credentials belonging to hundreds of network operators are being traded on the Dark Web. This disturbing finding highlights the cybersecurity risks facing telecommunications companies and internet infrastructure providers.
The report comes on the heels of a major cyberattack in early January against Spanish telecom carrier Orange España. In that incident, a hacker known as 'Snow' hijacked Orange España's account with RIPE NCC, the regional internet registry for Europe. After gaining access, Snow was able to sabotage the company's BGP and RPKI configurations, causing a 3-hour outage that disrupted services for customers.
@orange_es Meow meow meow! I have fixed your RIPE admin account security. Message me to get the new credentials :^) pic.twitter.com/NKFFDWb0Ec
— Snow 🏳️⚧️ (@Ms_Snow_OwO) January 3, 2024
According to Resecurity, the Orange España breach was enabled by network operator credentials that were likely stolen through an infostealer infection on an employee's computer back in September 2022.
In the wake of the high-profile Orange España attack, Resecurity investigated underground markets on the Dark Web and shockingly identified over 1,572 compromised customers of RIPE NCC customer accounts being sold by cybercriminals.
 |
| Image- Resecurity |
According to Resecurity, there has been a spike in infostealer infections targeting the users of RIPE and other regional registries like the Asia-Pacific Network Information Centre (APNIC), the African Network Information Centre (AFRINIC), and the Latin America and Caribbean Network Information Center (LACNIC). Left unchecked, these stolen operator credentials could enable disruptive cyberattacks that sabotage core network infrastructure.
Essentially, by gaining control of a network operator's account, a threat actor could alter routing configurations or other settings that keep traffic flowing properly. For example, they could manipulate BGP and RPKI data to reroute or block traffic, potentially causing massive outages similar to the Orange España incident.
Resecurity identified multiple postings on the Dark Web that show cybercriminals selling access to credentials belonging to telecom network administrators and engineers from various companies.
 |
| image- Resecurity |
In some cases, credentials on underground markets were offered for just $10.
Some of the independent actors were also offering higher-priced RIPE credentials. These higher value credentials included cookies, proxy, or remote access that could be activated via the deployment of malicious code onto the victim’s device.
Resecurity acquired 1,572 compromised access credentials to RIPE customer portals, some of which didn't have 2FA enabled.
 | |
|
 |
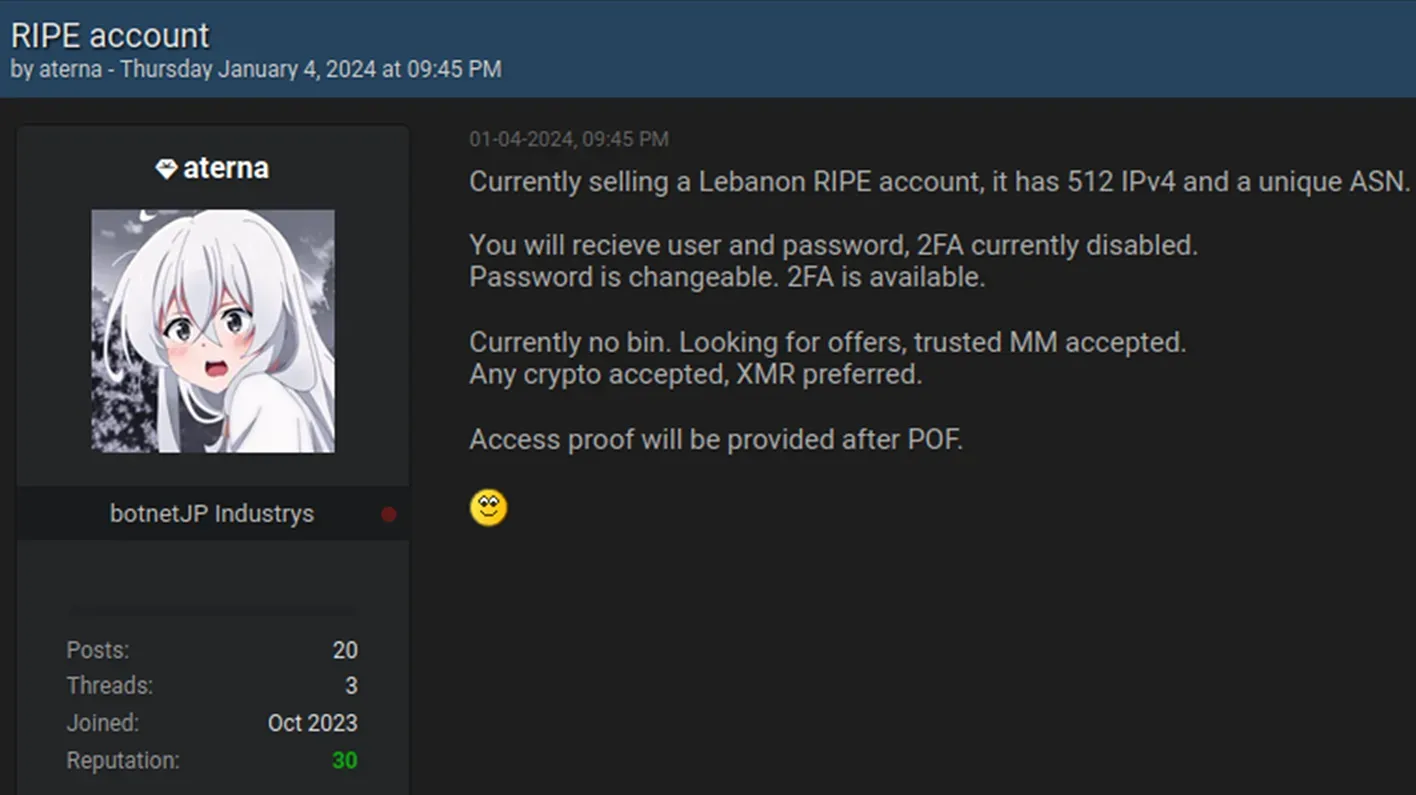
| POC compromised RIPE Account |
An example of a critical risk that could arise from this niche market could manifest via the collaboration between initial access brokers (IABs) and ransomware groups. The former could enable the latter to acquire the credentials of a compromised network engineer from one of the Indonesian ISPs and later use it to stage a more devastating attack inspired by the Orange España breach.
Network operators make prime targets because their access privileges allow them to manage internet number resources and make changes to routing systems. However since many use insecure practices like poor password hygiene and lack of multi-factor authentication (MFA), their accounts are prone to takeover by criminals.
In response to inquiries regarding the lack of mandatory two-factor authentication, RIPE stated that they were accelerating the implementation of 2FA by making it mandatory for all RIPE NCC Access accounts as soon as possible, - Resecurity blog reads
Some of the Identified Victims
According to the Resecurity, some identified victims were associated with significant organizations, including:
- Scientific research organization from Iran;
- Major financial organization from Kenya;
- One of the largest IT consulting firms in Azerbaijan, known for offering services like telecommunications, integrated network, and cloud solutions to enterprises and government entities;
- A major financial organization in Spain;
- One of the largest gambling providers in EU;
- ICT technology provider based in Saudi Arabia;
- An Israeli communications satellite operator;
- A government agency from Iraq;
- A nonprofit Internet Exchange (IXP), established in Riffa, located in the Southern Governorate of Bahrain.
Meanwhile, enterprises should check that their network engineers and IT staff are using best practices for access management, monitoring for signs of infection, and watching for exposed credentials on the Dark Web.
In the analysis conducted by Resecurity, the precursors of potential breaches were scrutinized across four prominent regional Internet service registries catering to enterprise customers. The examined organizations include:
| RIPE Registry | Compromised Accounts |
|---|---|
| RIPE (access.ripe.net) | 1572 |
| APNIC (my.apnic.net) | 84 |
| AFRINIC (my.afrinic.net/login) | 102 |
| LACNIC (milacnic.lacnic.net/lacnic/login) | 84 |
These entities play a crucial role in providing Internet number resources and registration services, thereby contributing to the seamless global operation of the web.
Above all, the Resecurity report highlights that the entire digital infrastructure sector faces an elevated risk of disruptive cyberattacks. With hundreds of compromised operator credentials now accessible to malicious actors, companies must take urgent steps to lock down internal access controls and identify potential security gaps.
By working together across the public and private sectors, cybersecurity experts hope to reduce the chances of a major infrastructure-crippling event. But as nation-state hacking and cyber warfare continue to intensify, many experts fear such an attack could be imminent.