
The vulnerability named MyFlaw by the Guardio research team, is a remote code execution vulnerability that exists due to Opera's 'My Flow' feature, which enables seamless sharing of notes and files between desktop and mobile through the browser. Specifically, the web-based chat interface for My Flow added an 'OPEN' link for any attached files, allowing them to be executed directly from the browser.
While convenient, this opened up concerning attack possibilities. As detailed by researchers, the ability to execute local system files from a web context signalled a high potential for security risks.
Further investigation revealed that My Flow's functionality stems from a preinstalled, built-in browser extension called 'Opera Touch Background'. This extension has extensive permissions, including the ability to open and download files to the local system.
Researchers found that web resources under Opera-controlled domains could communicate with this powerful extension using the chrome.runtime.connect API. Malicious abuse of this would enable file download and execution on the victim's computer.
Initial exploitation attempts using common techniques like cross-site scripting (XSS) were blocked due to Opera's security improvements. The team also found extensions were prevented from injecting scripts into Opera domains.
The breakthrough came upon discovering outdated, vulnerable assets under the *.flow.opera.com domain family. Specifically, an old version of the My Flow landing page lacked key security headers like CSP and SRI that would have blocked code injection.
Researchers confirmed they could abuse this forgotten page to inject code and simulate a device pairing that downloaded and executed payloads.
While this attack flow initially required a click event, researchers found a clever way to engineer it into a simple one-click attack. By presenting users with a routine "Thanks for Installing" notification after adding a disguised malicious extension, they could prompt a click anywhere on the page, triggering the exploit instantly.
Proof of Concept Demonstrates Alarming Potential
The team created a proof of concept (PoC) attack to demonstrate the real danger. It begins with an extension disguised as an ad blocker to encourage installs. Once added, it injects code into a vulnerable Opera domain asset, delivers the malicious payload, and executes it within one second.
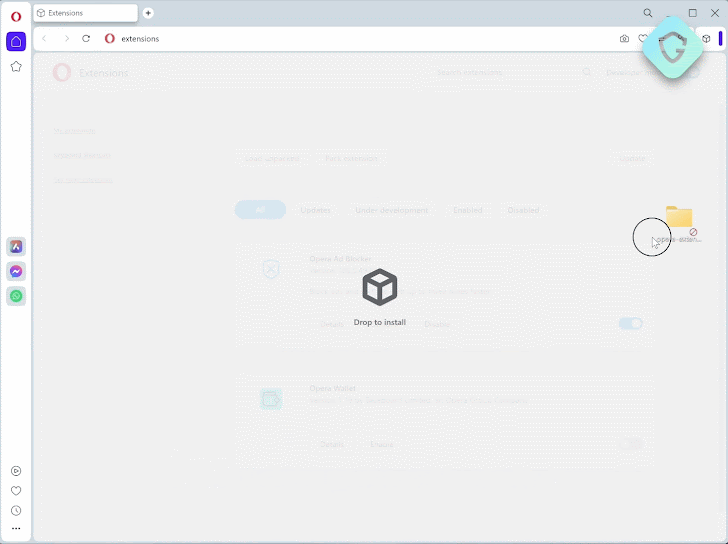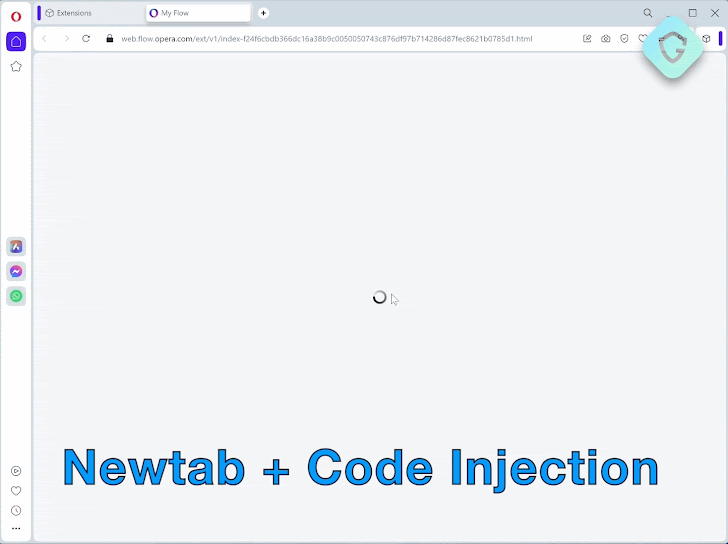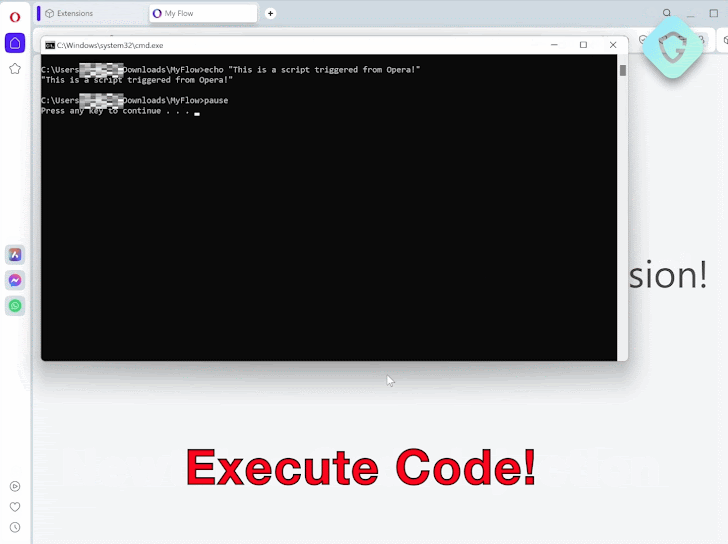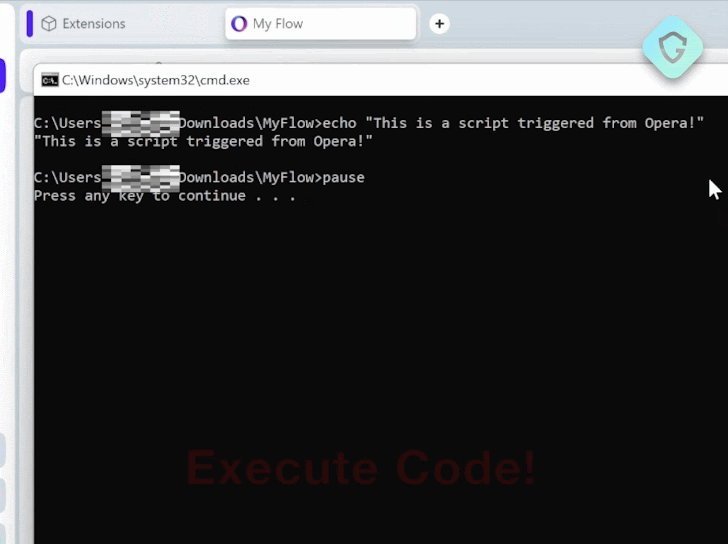 |
| Exploit POC Extension |
This rapid stealth execution highlights the alarming implications of this browser vulnerability.
Guardio Labs immediately disclosed full details to the Opera security team upon discovery of the flaw in November 2023. Within just 5 days, Opera implemented a fix by removing the insecure assets.
Opera stated they will continue monitoring and improving security to prevent similar issues. They thank Guardio Labs for the responsible disclosure and collaboration.
While no longer actively exploitable, researchers caution that risks remain due to the complexity of modern browser architectures. The report calls for more focus on disabling extension permissions on production domains and further isolating browser components.
This work underscores the constant evolution of browser exploitation techniques, despite security improvements. Hackers continue looking for creative ways to weaponize new features and bypass protections using extensions and other tools.