
A team of researchers from Ruhr University Bochum in Germany have uncovered new security vulnerabilities in the Secure Shell (SSH) protocol that could allow attackers to compromise the integrity of SSH connections.
The vulnerability named Terrapin Attack identified as (CVE-2023-48795, CVSS score: 5.9), the exploit has been described as the "first-ever practically exploitable prefix truncation attack."
SSH is a network protocol used to securely access remote servers and services over an unsecured network. It uses encryption to secure the connection and authenticate the server. SSH is widely used by system administrators and developers to manage servers and infrastructure.
The researchers found two core issues with SSH that undermine the integrity of the encrypted message stream:
- SSH does not fully authenticate the initial handshake between the client and server. This allows an attacker to inject messages and manipulate the sequence numbers used to verify packet order.
- SSH does not reset the sequence numbers when encryption keys are activated. So any manipulation of the numbers before encryption remains valid within the secure channel.
By exploiting these flaws, the researchers demonstrate a "prefix truncation attack" where an attacker can delete encrypted packets from the start of an SSH session without detection. Neither the client nor the server will notice the missing packets.
Terrapin Attack (CVE-2023-48795) Overview
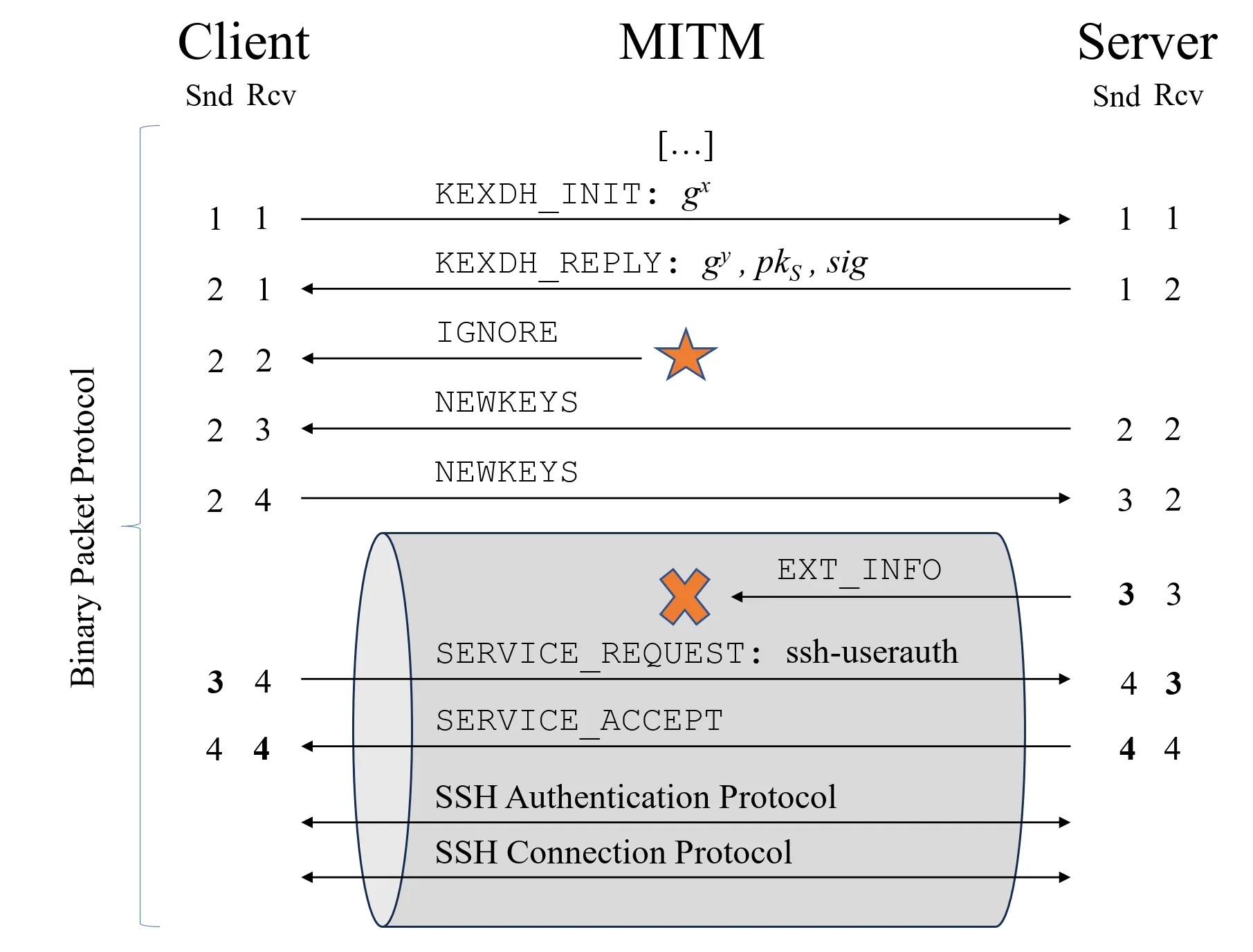 |
| Terrapin Attack overview |
There are two vulnerable OpenSSH configurations:
- ChaCha20-Poly1305
- Any aes(128|192|256)-cbc ciphers using the default MACs (or any MAC that uses Encrypt-then-MAC, EtM, for example – [email protected]).
The default OpenSSH client and server are vulnerable to this attack, as they are configured to allow the vulnerable ChaCha20-Poly1305 cipher.
Practical Implications of the Attack
The researchers showcase several practical ways the prefix truncation attack could be used:
- Downgrade the key exchange and authentication algorithms supported by tricking the client about the server's capabilities.
- Disable recent countermeasures in OpenSSH 9.5 that protect against keystroke timing attacks during password entry.
- Redirect a user's SSH login on AsyncSSH into an attacker-controlled shell, gaining complete control over the session.
- Replace the client's extension negotiation message with one chosen by the attacker to manipulate the session.
Through an internet-wide scan, the researchers found that 77% of SSH servers support a vulnerable encryption mode, making them potentially susceptible.
Root Causes Identified in SSH Design
According to the analysis, the root causes that introduce these flaws are:
- The SSH handshake does not authenticate the full transcript, only selective parts. This allows unsupported messages to be injected by a MitM.
- SSH was designed to increment sequence numbers monotonically throughout a connection. Resetting the sequence numbers when keys change was not part of the original design.
These weaknesses were not previously exploited because new encryption modes and protocol extensions added over the years began interacting in unforeseen ways, exposing the underlying vulnerabilities.
The researchers recommend two primary changes to the SSH specification to address the issues:
- Reset sequence numbers to zero when encryption keys are activated. This prevents manipulation of numbers during the handshake from affecting the secure channel.
- Authenticate a hash of the full handshake transcript at the start of the secure channel, similar to the Finished messages in TLS. This detects any MitM tampering with the handshake.
For clients and servers today, the vulnerabilities can be mitigated by avoiding vulnerable encryption algorithms like ChaCha20-Poly1305 and CBC-EtM which are affected by the attack. However, fixing the root causes in the protocol is advised for a long-term solution.
The Terrapin Attack provides significant new insights into weaknesses in the decades-old SSH protocol that have relevance for real-world security today. Combined with the prevalent use of SSH for remote administration and automation, the issues highlighted should warrant prompt attention from protocol designers, implementers, and end-users to mitigate risks.
While SSH has proven resilient over its lifetime, the research illustrates the difficulty in designing secure cryptographic protocols that maintain robustness against perturbation and unforeseen usage scenarios. The findings underscore the necessity of continual cryptographic review and improvement to meet modern security demands.
SSH may benefit from a formal redesign effort guided by the latest attack research to simplify the sprawling protocol and ensure it meets today’s security and functionality needs. Nonetheless, the Terrapin Attack paper [PDF] delivers a potent reminder that even entrenched standards require ongoing scrutiny and evolution to keep pace with the ever-changing security landscape.