
Palo Alto Networks has disclosed multiple critical vulnerabilities in its Expedition tool that could allow attackers to hijack PAN-OS firewalls.
According to the advisory published on Wednesday, flaws include unauthenticated command injection and SQL injection vulnerabilities.
Expedition, a tool designed to facilitate the migration of configurations from vendors like Checkpoint and Cisco to Palo Alto Networks' systems, was found to contain five severe security issues. These vulnerabilities tracked as CVE-2024-9463, CVE-2024-9464, CVE-2024-9465, CVE-2024-9466, and CVE-2024-9467, collectively allow attackers to access sensitive data, execute arbitrary commands, and potentially take over firewall admin accounts.
- CVE-2024-9463 (unauthenticated command injection vulnerability)
- CVE-2024-9464 (authenticated command injection vulnerability)
- CVE-2024-9465 (unauthenticated SQL injection vulnerability)
- CVE-2024-9466 (cleartext credentials stored in logs)
- CVE-2024-9467 (unauthenticated reflected XSS vulnerability)
The most critical of these flaws, CVE-2024-9463, received a CVSS score of 9.9 out of 10. This unauthenticated command injection vulnerability enables attackers to run arbitrary OS commands as root on the Expedition system, potentially leading to the disclosure of usernames, cleartext passwords, device configurations, and API keys for PAN-OS firewalls.
Zach Hanley, a vulnerability researcher at Horizon3.ai, discovered four of the five vulnerabilities while investigating a previously disclosed flaw (CVE-2024-5910) in the Expedition application. Hanley's research, detailed in a blog post, reveals how these vulnerabilities can be chained together to achieve full system compromise.
Hanley's analysis demonstrates how an attacker could exploit CVE-2024-5910 to reset admin credentials and then leverage CVE-2024-9464 (an authenticated command injection flaw) to gain root access to the Expedition server.
This attack chain effectively transforms an authenticated vulnerability into an unauthenticated one, significantly increasing the potential impact.
Furthermore, Hanley uncovered an unauthenticated SQL injection vulnerability (CVE-2024-9465) that allows attackers to extract sensitive information from the Expedition database, including password hashes, usernames, and device API keys. This flaw could also be used to create and read arbitrary files on the system.
Perhaps most alarmingly, Hanley discovered that Expedition was storing cleartext credentials in debug logs (CVE-2024-9466), potentially exposing firewall usernames, passwords, and API keys to any attacker who gains access to the system.
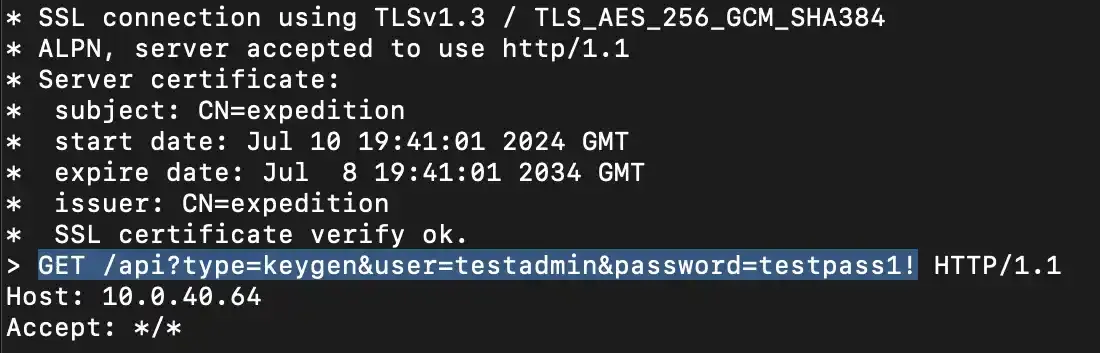 |
| debug.txt logging cleartext credentials |
While Palo Alto Networks states that they are not aware of any malicious exploitation of these vulnerabilities in the wild, the public disclosure of these flaws and the release of proof-of-concept exploit code by Horizon3.ai significantly increases the risk of attacks.
Palo Alto Networks has released patches for all the reported vulnerabilities in Expedition version 1.2.96 and later. The company strongly advises customers to update immediately and take additional precautions:
- Rotate all Expedition usernames, passwords, and API keys after upgrading.
- Rotate all firewall usernames, passwords, and API keys that have been processed by Expedition.
- Restrict network access to Expedition to only authorized users, hosts, or networks.