
SafeBreach Labs researchers have published the first proof-of-concept exploit for CVE-2024-49113, a critical vulnerability affecting Windows Server systems that could allow attackers to crash unpatched domain controllers through a denial-of-service attack.
The vulnerability, discovered by Yuki Chen and initially disclosed on December 10, 2024, affects the Windows Lightweight Directory Access Protocol (LDAP) implementation.
SafeBreach Labs researchers Or Yair and Shahak Morag demonstrated that the flaw impacts domain controllers and all unpatched Windows Server installations.
The exploit requires no authentication and only needs the victim's DNS server to have Internet connectivity.
The attack chain involves seven steps, beginning with a DCE/RPC request to the target server and culminating in a crash of the Local Security Authority Subsystem Service (LSASS), forcing a system reboot.
"The vulnerability that the SafeBreach Labs PoC exploits affects technology that is in widespread use across enterprise networks, and this flaw could help attackers propagate more easily and effectively," the researchers noted in their detailed technical analysis.
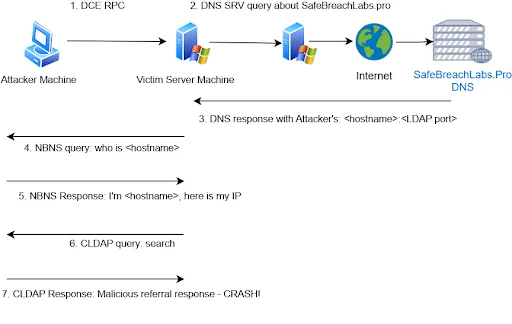
The attack leverages a combination of DNS SRV queries and LDAP referral responses to trigger the vulnerability. Specifically, it entails sending a DCE/RPC request to the victim server, ultimately causing the Local Security Authority Subsystem Service (LSASS) to crash and force a reboot when a specially crafted CLDAP referral response packet with a non-zero value for "lm_referral" is sent.
While Microsoft has released patches for both CVE-2024-49113 and a related remote code execution vulnerability (CVE-2024-49112), SafeBreach Labs warns that organizations should prioritize patching, as their research indicates that the same attack vector could potentially be leveraged for remote code execution in the future.
The researchers verified that Microsoft's patch effectively prevents the exploitation by fixing an out-of-bounds vulnerability in the wldap32.dll component.
For organizations that cannot immediately patch their systems, it is recommended to implement detection mechanisms for:
- Suspicious CLDAP referral responses
- Unusual DsrGetDcNameEx2 calls
- Suspicious DNS SRV queries
The vulnerability affects multiple Windows Server versions, with researchers confirming successful exploitation on Windows Server 2019 and 2022. SafeBreach Labs has published its proof-of-concept code in a research repository to help organizations test their systems' vulnerability status.
Organizations are strongly advised to review their Windows Server installations and apply the necessary security updates to prevent potential exploitation.