
The group has been observed using a deceptive approach that tricks targets into executing malicious code through Windows PowerShell with administrator privileges.
The attack begins with sophisticated social engineering, where the threat actors pose as South Korean government officials to establish rapport with their targets. After building trust, they launch a spear-phishing campaign, sending emails containing PDF attachments. When targets attempt to access these PDFs, they are directed to a registration page that provides step-by-step instructions for running PowerShell as an administrator and executing the provided code.
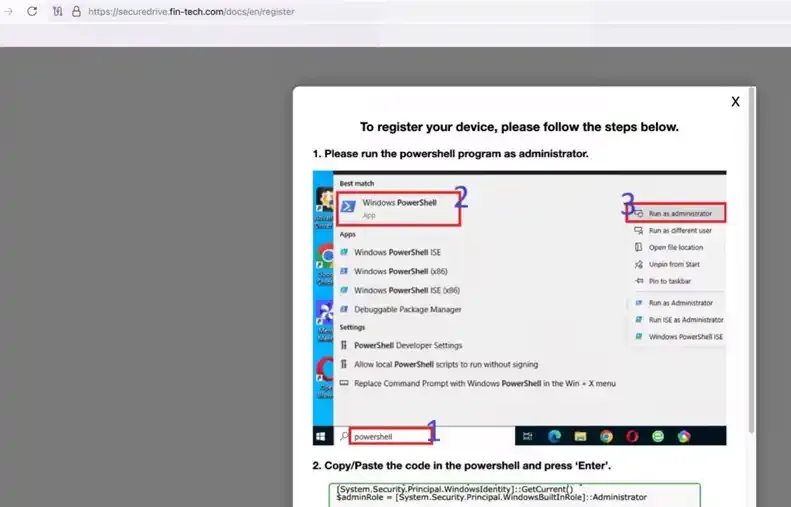 |
| Tricking targets into running PowerShell as an administrator and then pasting and running code provided by the threat actor |
Once the malicious code is run with administrator privileges, it initiates a multi-stage attack. The code downloads and installs a browser-based remote desktop tool and retrieves a certificate file containing a hardcoded PIN from a remote server.
The final stage involves sending a web request to register the compromised device using the downloaded certificate and PIN, ultimately giving the threat actors remote access for data exfiltration.
Microsoft Threat Intelligence has observed North Korean state actor Emerald Sleet (also known as Kimsuky and VELVET CHOLLIMA) using a new tactic: tricking targets into running PowerShell as an administrator and then pasting and running code provided by the threat actor. pic.twitter.com/PTcxwhBhGn
— Microsoft Threat Intelligence (@MsftSecIntel) February 11, 2025
Microsoft reports that while this tactic has only been observed in limited attacks since January 2025, it represents a significant evolution in Emerald Sleet's methodology.
The group primarily targets individuals working in international affairs, particularly those focused on Northeast Asia, as well as NGOs, government agencies, and media organizations across North America, South America, Europe, and East Asia.
To combat these threats, Microsoft Defender XDR now includes detection capabilities for Emerald Sleet's activities.
The company recommends implementing advanced anti-phishing solutions, conducting user training about phishing risks, and employing attack surface reduction rules to prevent malicious script execution. Microsoft also actively notifies customers who have been targeted or compromised by such nation-state activities.